Computerized Adaptive Testing (CAT) is a form of assessment in which administered items are selected based on the ability levels of the students. Initial item selection is typically based on the assumption that the test taker is of average ability; subsequently selected items are based on ability estimates obtained from preceding responses. This approach optimizes precision by increasing the selection of items that are neither too easy nor too difficult. CAT is efficient and quickly identifies gaps in student learning.
Even better is the fact that ATI automates the construction of computerized adaptive tests. Tests are generated by ATI from an Assessment Planner that defines the item pool to be used in selecting items for the adaptive assessment. Automated construction provides ATI the capability to generate customized computerized adaptive tests to meet unique district needs.
The Galileo Computerized Adaptive Testing Pilot is an integral part of ATI’s next generation comprehensive assessment system and is completely integrated into ATI’s Galileo K-12 Online Instructional Improvement System. Adaptive assessments serve many purposes including guiding instruction, monitoring progress, screening, and assisting in placement decisions.
Integration within Galileo ensures that teaching staff and administrators have easy and rapid access to the full range of innovative assessment, reporting, curriculum, and measurement tools provided all within one system. ATI’s comprehensive assessment system is part of our ongoing commitment to continuous innovation so that school districts and charter schools can continuously build their own capacity to lead change in ways that enhance the quality and impact of education on our nation’s children and youth.
ATI's approach to Computerized Adaptive Testing is discussed in greater depth in Composition of a Comprehensive Assessment System.
Experience Galileo during an online overview and see how it provides a better way to address the goal of raising student achievement. You can visit the Assessment Technology Incorporated website (ati-online.com), participate in an online overview by registering either through the website or by calling 1.877.442.5453 to speak with a Field Services Coordinator, or visit us at the
• Colorado Association of School Boards (CASB) 71st Annual Conference December 8 through 11 at the Broadmoor Hotel, Colorado Springs, Colorado.
• Arizona School Boards Association (ASBA)/ Arizona School Administrators (ASA) 54th Annual Conference December 15 through 16 at the Biltmore Conference Center, Phoenix, Arizona.
Monday, November 28, 2011
Monday, November 21, 2011
Data Access Protection By Cloud-Based Service Providers
In an earlier post, I discussed some key benefits of cloud-based services, or Software as a Service (SaaS). While the benefits are significant, there are risks that must be considered when making decisions about SaaS.
To approach these risks and some of the questions prospective users of cloud-based services might ask, it is easiest to break the risks down into categories. In today’s post, I’ll take a look at two key questions potential SaaS users might have about data access control and protection:
- How can data be kept safe from unauthorized access? Whether a cloud-based service is used for student information systems (SIS), instructional improvement systems (IIS), data warehousing or more than one, ensuring the protection of sensitive student data is taken seriously by educators and the vendors providing these services. Effective implementation of security measures in the following areas provides protection for externally-stored student data on par with the security achieved by housing data on internal servers:
- Security Hardware: Security hardware includes firewalls that filter network traffic to (and from) application and data servers and inspect each packet for a threat, dropping traffic when a threat is present. Another effective type of security hardware is load balancers or cache engines that offload direct access to application servers and prevent operating system exploits.
- Security Software: The baseline of any effective secure software environment includes up-to-date operating systems on all application and data servers. Microsoft revealed in the first half of 2011, less than one percent of the exploits discovered took advantage of a “zero day vulnerability” (one that had not yet been patched by the vendor). This means over 99 percent of the attacks were preventable merely by maintaining well-patched operating systems and software. Also falling in the category of security software is the antivirus and computer security software suite. Finally, effective use of change management software can help SaaS Information Technology (IT) staff informed about any attempts to alter the application server environment without their knowledge.
- Secure Network Architecture: A well-designed network for any application-hosting environment includes segregation of application and data servers. This can be achieved by physically segmenting traffic or using a combination of segmentation and security hardware.
- Data Encryption: Encrypting the transport of data from the service vendor to the client system is critical. The current best practice for Secure Sockets Layer (SSL), Transport Level Security (TLS) is to employ a minimum of 128-bit encryption.
- Physical Security: An easily overlooked security concern is the physical environment of the service provider. Are application and data servers housed within a secure environment, and is access to the environment regulated by the vendor? Physical controls include personnel monitoring, multi-factor access authentication, external monitoring and other types of surveillance.
- How can SaaS vendors prevent authorized users from accessing data they shouldn’t? It’s an easy problem to develop. Energy is focused on keeping the bad guys out, but once credentials are provided to trusted users, controls over proper access are overlooked. Even with proper physical and network controls, IT personnel are often leery of relinquishing data access control to an external system. This is because the outsourced services often effectively bypass the security controls implemented internally, at least to some degree. Two primary types of external security models may be implemented:
- Hierarchical - Such as the user account structure employed by Galileo Online IIS. Users are allowed access to increasing levels of information dependent upon the scope of the user account.
- Access-based - A flatter model such as that employed by Google Documents. Discrete permissions are assigned to individual data objects on a per-user, or per-group, basis.
User privileges can be managed effectively and in some cases there is even benefit to a separate permissions structure because individual changes can be managed by the users of the system instead of having to rely on technical staff to implement changes.
Do you have other concerns about data access protection that haven’t been covered? In a future post I’ll consider another risk area presented by use of cloud-based services and address how vendors are overcoming those challenges to create safe, effective environments for their clients.
Monday, November 14, 2011
A powerful and often overlooked tool....
Nested within the Aggregate Multi-Test Report and the Benchmark Results Report is one of Galileo’s most powerful tools for intervention: The Benchmark Profile.
The goal of the Benchmark Profile is to provide a detailed plan for moving an individual student or entire risk group to the next level of risk assessment.
There are two versions of the Benchmark Profile:
• Group Benchmark Profile
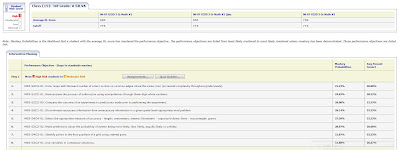
• Student Benchmark Profile
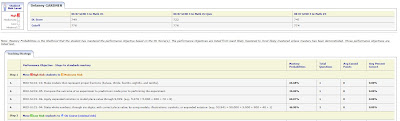
Features:
• Each standard will appear along with the probability that the student has mastered that standard, and their average score on questions covering that standard (Student Benchmark Profile only).
• Every student’s Developmental Level Score (or average for the group) as well as the cut score for each benchmark is displayed at the top of the profile.
• Profiles will continuously update after each assessment to give you a current view of student progress.
• Links to schedule Assignments and Quizzes directly from the report (Group Benchmark Profile only).
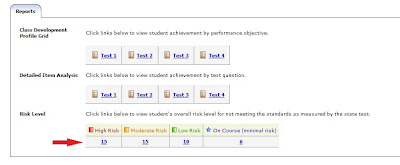
The Group Benchmark Profile can be accessed by going through the Benchmark Results Report:
• From the Reports Tab → Test Sets → Benchmark Results
• From the Dashboard → Benchmark Result (Under Recent Events)
From the Benchmark Results page you can simply select which risk category you would like to see a detailed plan for:
The Student Benchmark Profile can be accessed from within the Aggregate-Multi Test Report:
• From the Reports Tab → Multi Test → Aggregate Multi-Test
• Next Select the “View Detail Link”
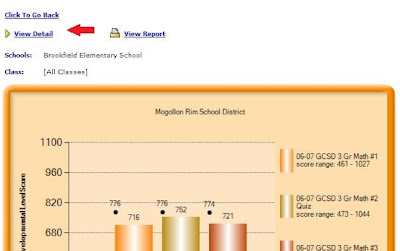
• Despite the fact that it may not look like it, everything on the next page will be linked. You can select the School/Class or Risk Category to see a list of students contained in your selection.
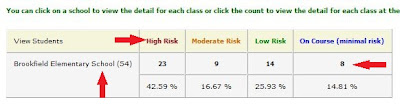
• By selecting a student you will bring up that individual’s customized benchmark profile.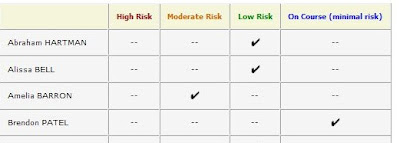
-Denny Armstrong, Field Services Coordinator
The goal of the Benchmark Profile is to provide a detailed plan for moving an individual student or entire risk group to the next level of risk assessment.
There are two versions of the Benchmark Profile:
• Group Benchmark Profile

• Student Benchmark Profile

Features:
• Each standard will appear along with the probability that the student has mastered that standard, and their average score on questions covering that standard (Student Benchmark Profile only).
• Every student’s Developmental Level Score (or average for the group) as well as the cut score for each benchmark is displayed at the top of the profile.
• Profiles will continuously update after each assessment to give you a current view of student progress.
• Links to schedule Assignments and Quizzes directly from the report (Group Benchmark Profile only).
The Group Benchmark Profile can be accessed by going through the Benchmark Results Report:
• From the Reports Tab → Test Sets → Benchmark Results
• From the Dashboard → Benchmark Result (Under Recent Events)
From the Benchmark Results page you can simply select which risk category you would like to see a detailed plan for:

The Student Benchmark Profile can be accessed from within the Aggregate-Multi Test Report:
• From the Reports Tab → Multi Test → Aggregate Multi-Test
• Next Select the “View Detail Link”

• Despite the fact that it may not look like it, everything on the next page will be linked. You can select the School/Class or Risk Category to see a list of students contained in your selection.

• By selecting a student you will bring up that individual’s customized benchmark profile.

-Denny Armstrong, Field Services Coordinator
Tuesday, November 8, 2011
Supporting National Head Start Association Accomplishments
As a long-time supporter of the National Head Start Association (NHSA), we would like to share a portion of a recent email from the Association that provided information on current media attention regarding their achievements.
The following are a selection of links to articles provided in the Head Start email.
Occupy the Classroom - Nicholas Kristof for the New York Times
From Kindergarten to College Completion - Judith Scott-Clayton for the New York Times’ Economix Blog
It Takes a Village - Charles M. Blow for the New York Times
ATI supports NHSA in several ways. One is the development of the Galileo Pre-K Online Portrait of Child Outcomes. This is a broad array of Head Start programs representing several states that have joined together for several years to create and share important stories about themselves and about children's accomplishments. The Portrait of Child Outcomes has been used by NHSA in making presentations nationwide documenting the contributions of Head Start to early childhood learning. We are privileged to have the opportunity to bring their story to you, click here.
We also support Head Start by continuously enhancing the tools offered to meet the changing needs of the program . For example, we have recently designed our new Galileo G3 Assessment Scales to align with the 2011 Head Start Child Development and Early Learning Framework, representing the developmental building blocks that are most important for a child’s school and long-term success. To learn more, click here.
Right now, there is a growing realization among business leaders and policy makers that investment in early childhood is key to the future success of our nation. There is also a greater understanding of the importance in the development of character of the first five years of life and a greater appreciation of the long term benefits to society from investing in high quality programs such as Head Start and Early Head Start. In recent weeks, national media coverage has made mention of Head Start repeatedly. We have always seen the value of the work we do, but it’s exciting to see others sit up and take note! We wanted to share some stories with you that you may enjoy and that may be useful to you in educating others in your community about Head Start.
The following are a selection of links to articles provided in the Head Start email.
Occupy the Classroom - Nicholas Kristof for the New York Times
From Kindergarten to College Completion - Judith Scott-Clayton for the New York Times’ Economix Blog
It Takes a Village - Charles M. Blow for the New York Times
ATI supports NHSA in several ways. One is the development of the Galileo Pre-K Online Portrait of Child Outcomes. This is a broad array of Head Start programs representing several states that have joined together for several years to create and share important stories about themselves and about children's accomplishments. The Portrait of Child Outcomes has been used by NHSA in making presentations nationwide documenting the contributions of Head Start to early childhood learning. We are privileged to have the opportunity to bring their story to you, click here.
We also support Head Start by continuously enhancing the tools offered to meet the changing needs of the program . For example, we have recently designed our new Galileo G3 Assessment Scales to align with the 2011 Head Start Child Development and Early Learning Framework, representing the developmental building blocks that are most important for a child’s school and long-term success. To learn more, click here.
Subscribe to:
Posts (Atom)
